TABLE OF CONTENT
Introduction
Our motto here at Zack's is to give credit where credit is due. This time, we must credit Tj for writing a great how-to article on full disk encryption on Ubuntu Linux. This guide is a "rewrite" of Tj's guide, but it is suited for Debian minimal installations.
We will walk you through the steps to enable disk encryption during the Debian Linux minimal installation, and we'll cover everything you need to know to keep your data safe from unauthorized access. While disk encryption can be set on any computer, it is more common on notebooks. Hypothetically, suppose someone steals your notebook with disc encryption in place. In that case, they will not be able to access the data on your disk nor boot the operating system without knowing the passphrase to unlock the disk.
By the end of this tutorial, you'll have a fully functioning Debian Linux minimal system and the peace of mind that comes with knowing your data is secure. Let's dive in and ensure your Debian installation is fortified with the power of disk encryption.
Prerequisites
You can follow that guide until the Disk Partitioning step, where we will start with the disk encryption configuration.
Before you start, make sure your computer or virtual machine is configured to start in UEFI mode. You can set that up in your computer's BIOS or in virtual machine settings. If you plan to install Debian either on a real computer or a virtual machine and you use Debian ISO image, once you boot from it, please select Advanced options from the installer menu, followed by Expert install. This way, you will ensure all installation options are available.
Disk Encryption Setup
Once you choose the language and locales and configure your keyboard, you will be presented with a menu option to Load installer components from installation media. Once there, please select (with the Space key on your keyboard) the following two options:
- crypto-dm-modules
- parted-udeb
Once selected, you can keep configuring all other options from the menu until you come to the Partition disks option. This is where you will start configuring the disk encryption.
Disk Partitioning - Stage 01
Partition disks
Execute a Shell
anna-install cryptsetup-udeb
anna-install lvm2-udeblsblkparted /dev/sdamklabel gptFor the partitions, you can create a "satisfy-all" basic set. Usually, I set the following partitions:
- Boot partition - size 1GB
- GRUB partition - size 2MB
- EFI System partition - size 128 MB
- Root FS partition - rest of the space on the disk
mkpart boot 1MiB 1025MiB
mkpart grub 1025MiB 1027MiB
mkpart EFI-SP 1027MiB 1155MiB
mkpart rootfs 1155MiB 100%quit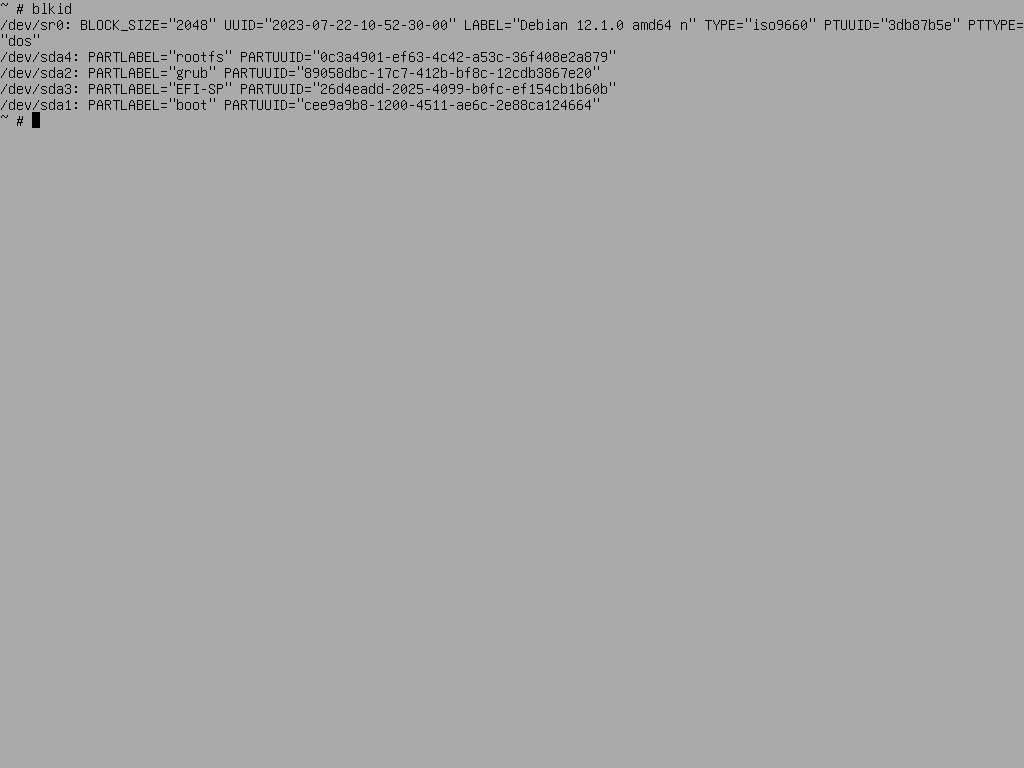
List Partitions
LUKS Encrypt
We will use the LUKS (Linux Unified Key Setup) encryption for full disk encryption... well, almost full. We will encrypt boot and rootfs partitions, which will not only encrypt all of the data on the disk but will also render the computer not being able to boot the operating system without knowing the passphrase to unlock the disk.
For the boot partition, you need to explicitly define LUKS version 1 type when enabling encryption because otherwise, the GRUB boot loader will not be able to install to or unlock the encrypted device. To do so, while still in the shell, execute the following:
cryptsetup luksFormat --type=luks1 /dev/sda1cryptsetup luksFormat /dev/sda4cryptsetup open /dev/sda1 LUKS_BOOT
cryptsetup open /dev/sda4 sda4_cryptls /dev/mapper/
control LUKS_BOOT sda4_cryptmkfs.ext2 -L boot /dev/mapper/LUKS_BOOT
mkfs.fat -F 16 -n EFI-SP /dev/sda3Root FS LVM Setup
pvcreate /dev/mapper/sda4_cryptvgcreate vgdebian /dev/mapper/sda4_cryptlvcreate -L 1G -n swap vgdebian
lvcreate -l 100%FREE -n root vgdebianexitDisk Partitioning - Stage 02

Partition Disks
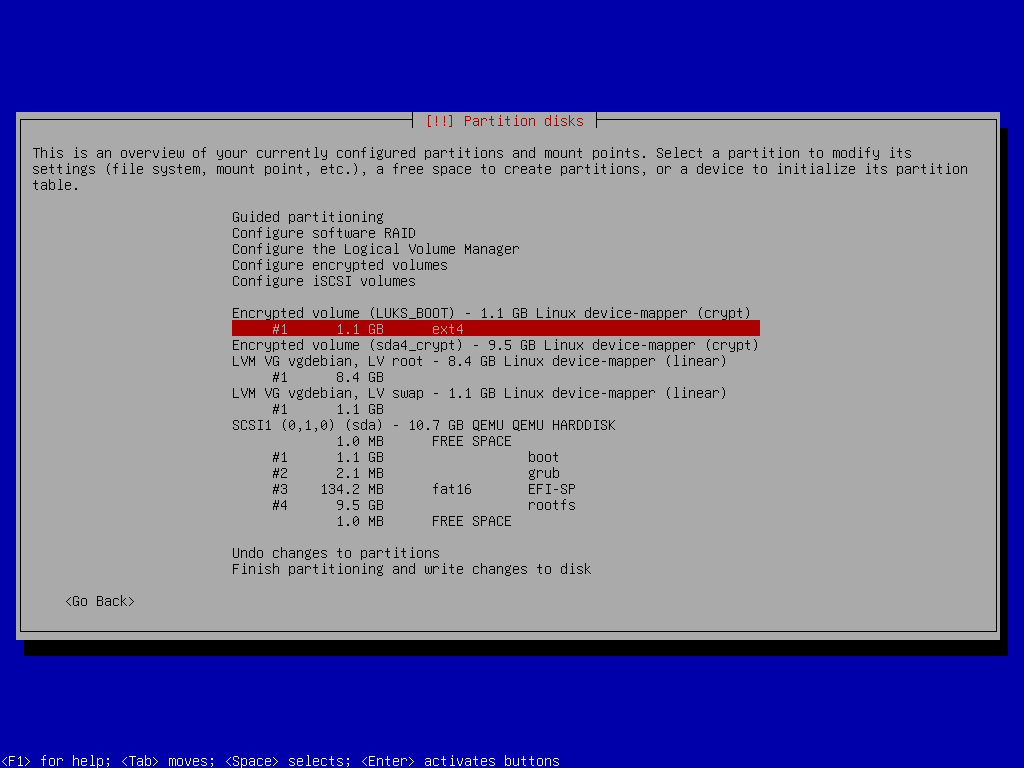
Boot Partition
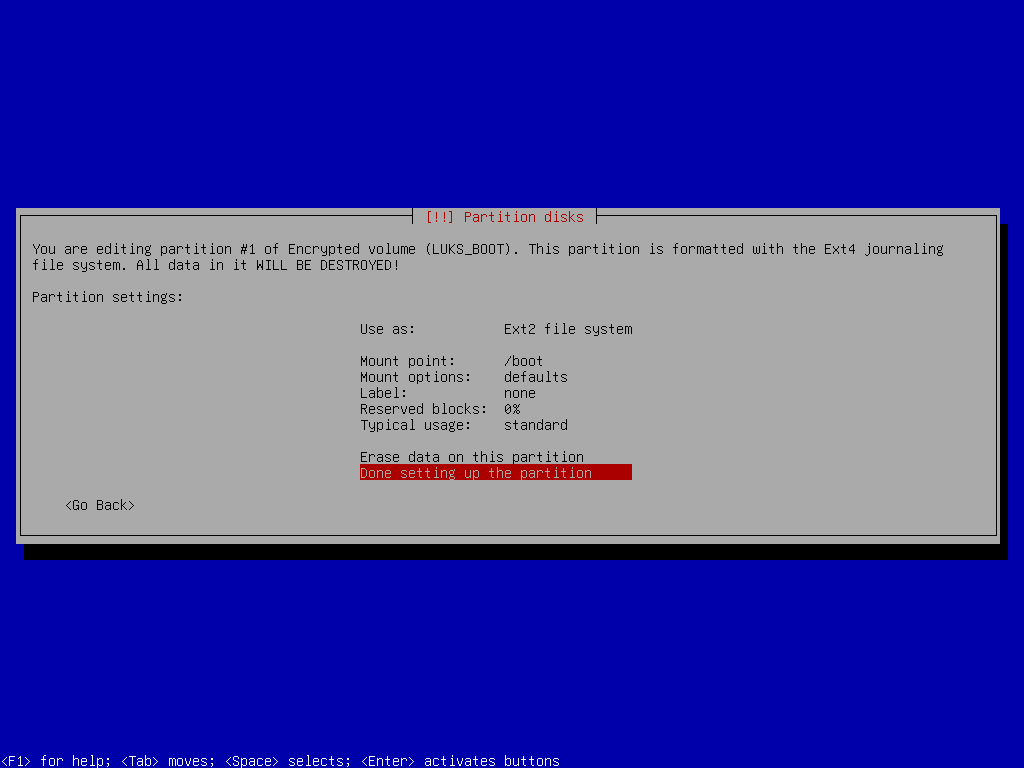
Boot Partition Setup
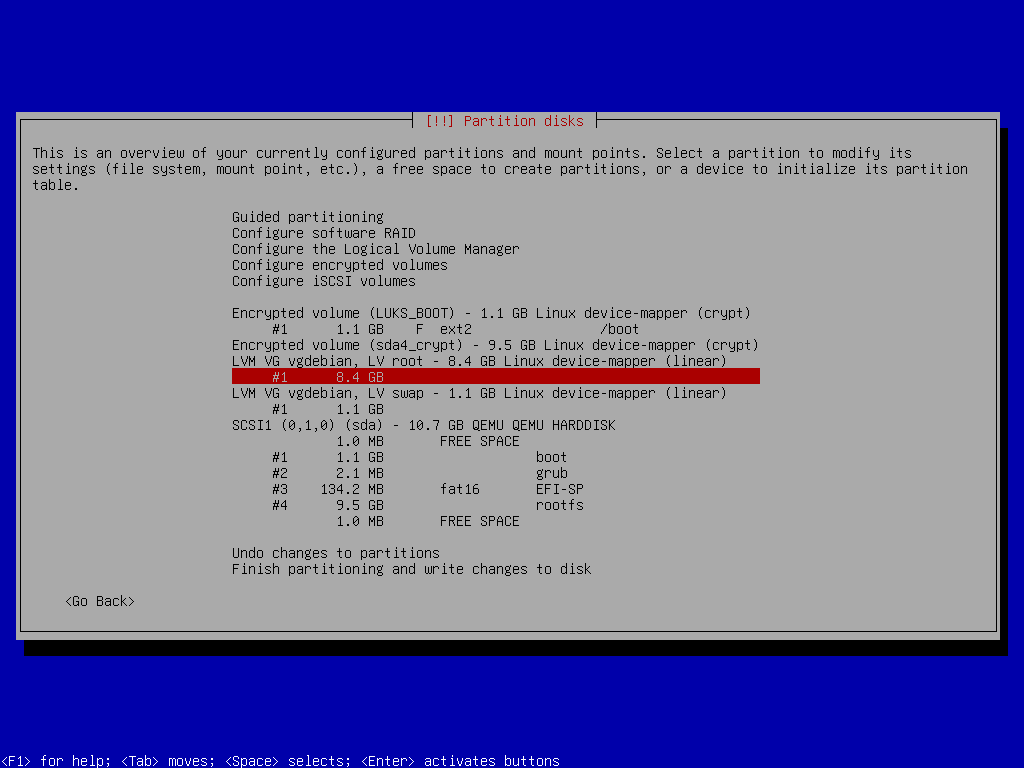
Root Partition
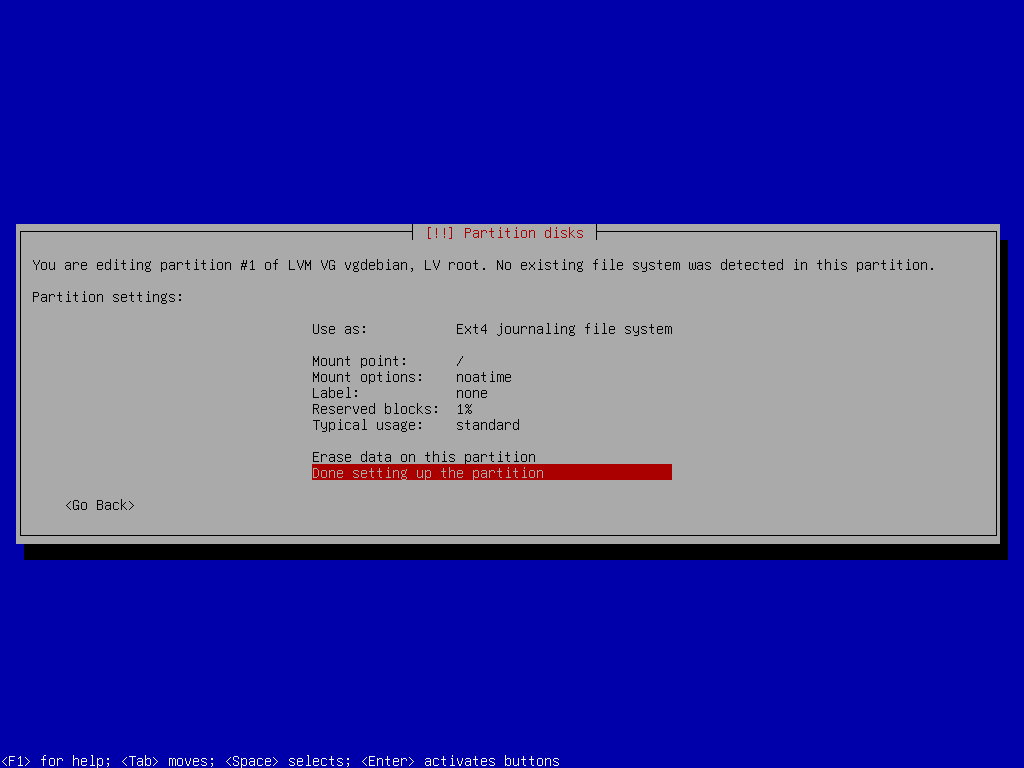
Root Partition Setup
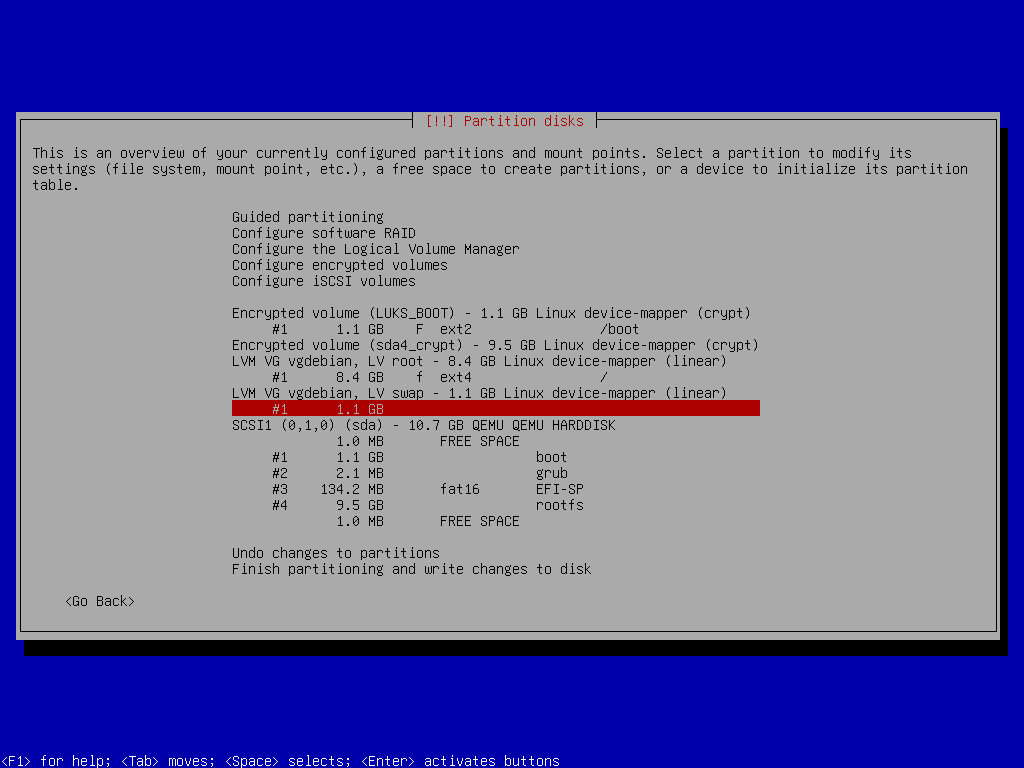
Swap Space
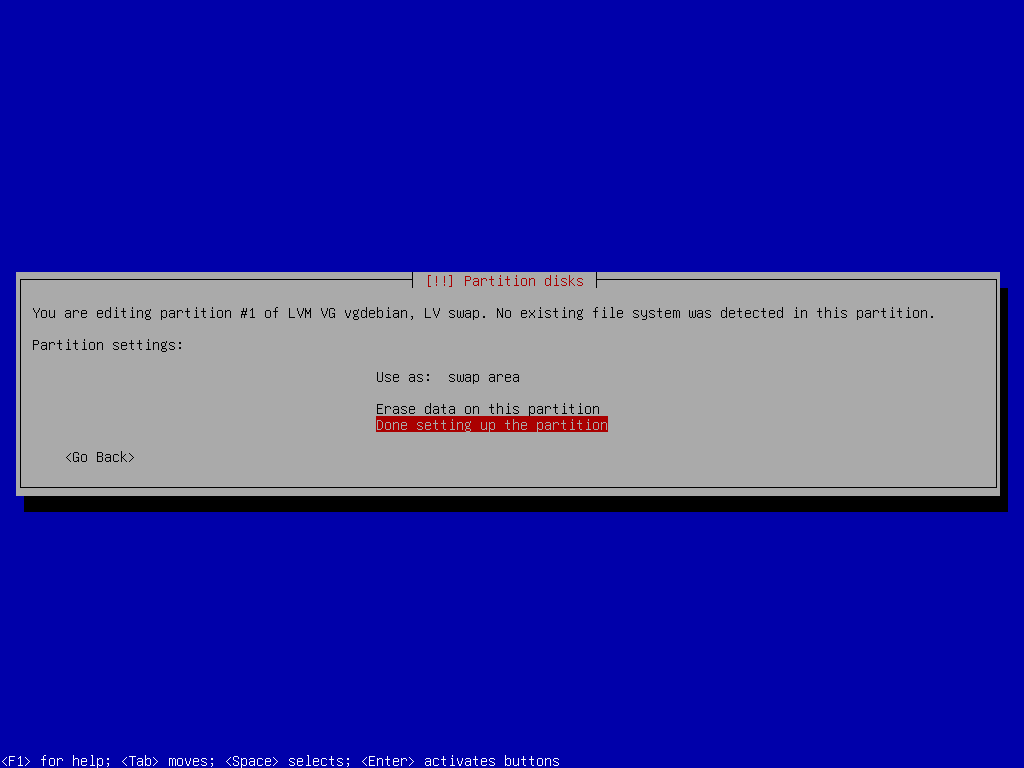
Swap Space Setup
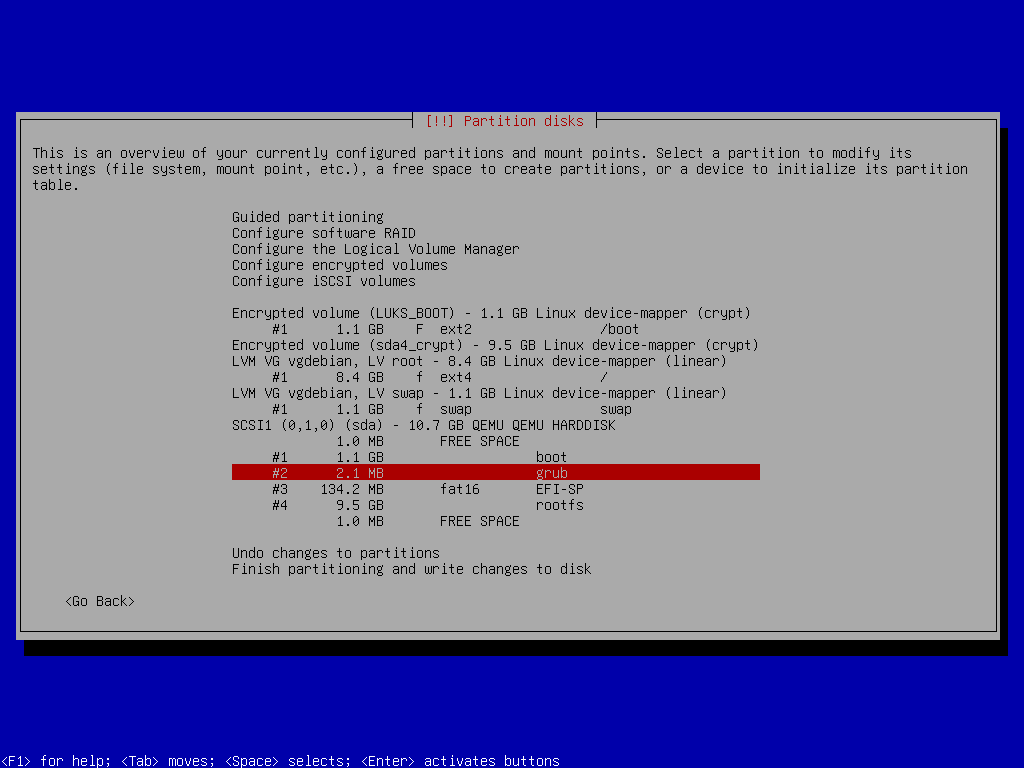
Grub Partition
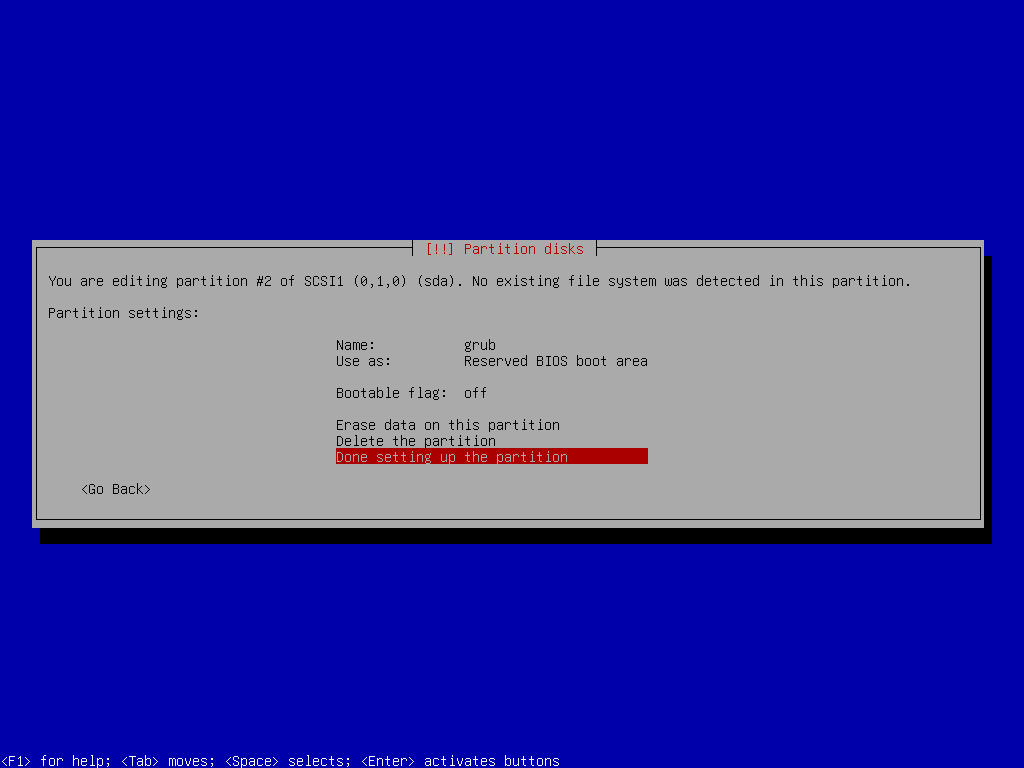
Grub Partition Setup
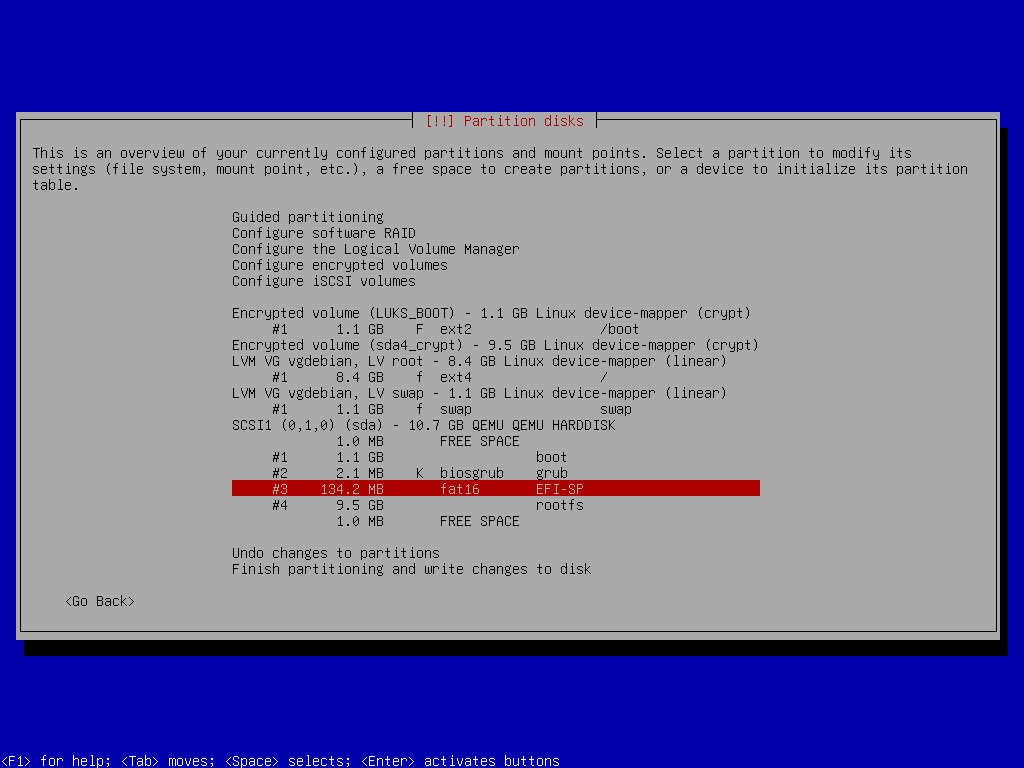
EFI-SP Partition
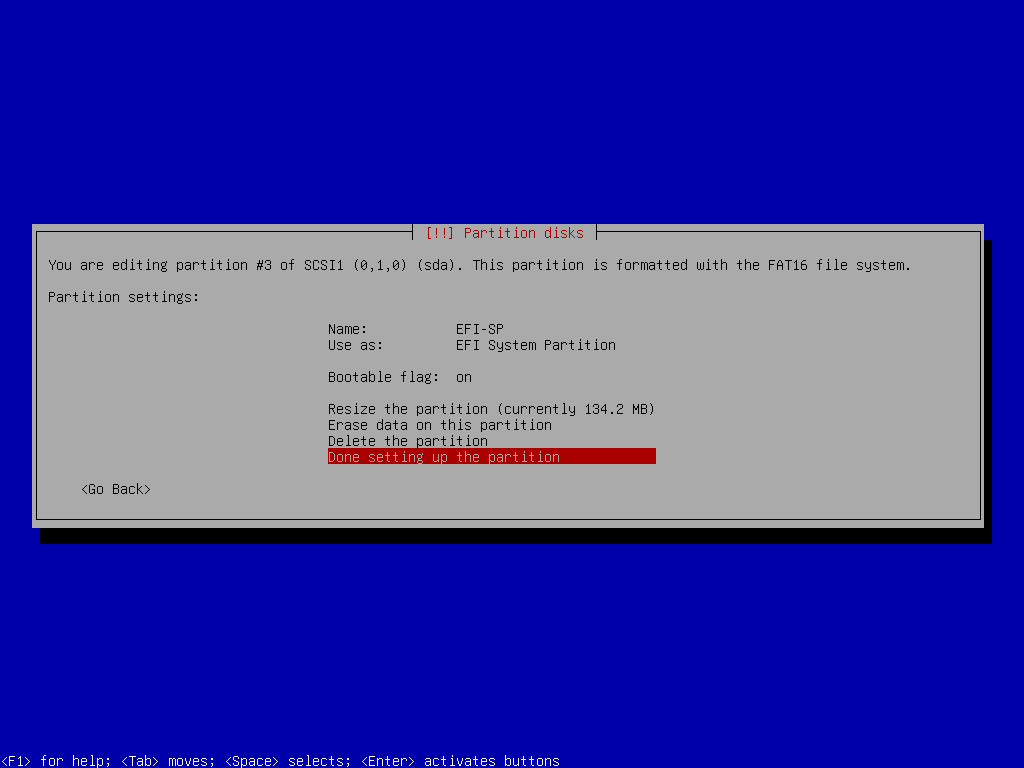
EFI-SP Partition Setup
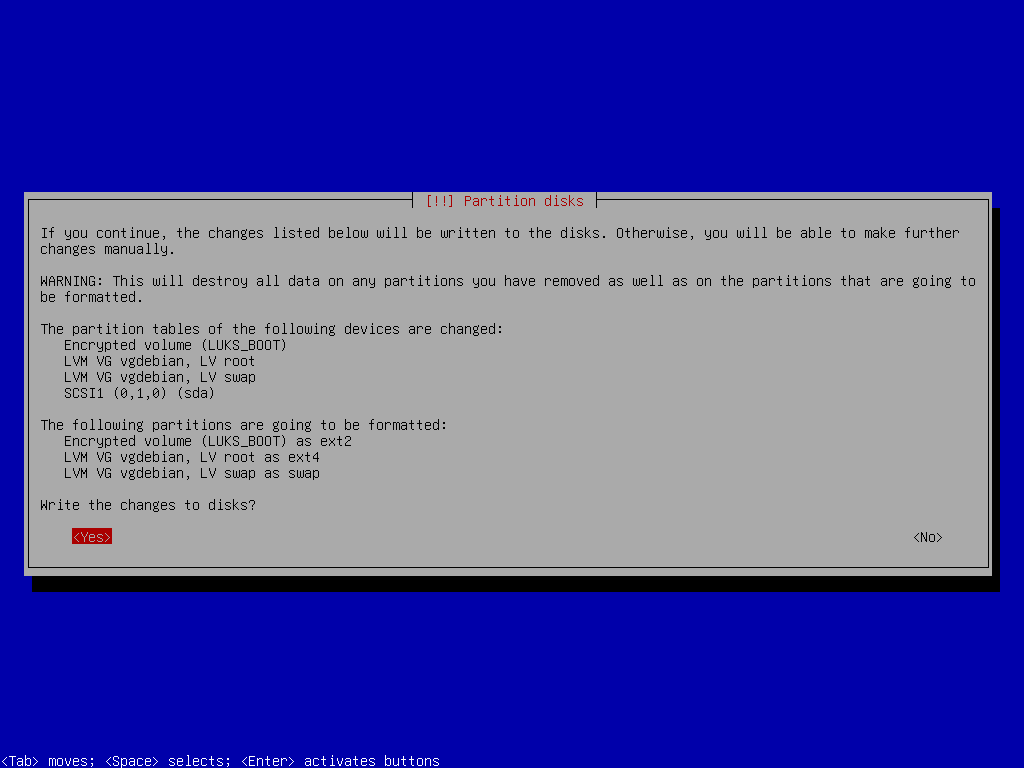
Write to Disk
System Install & GRUB Setup
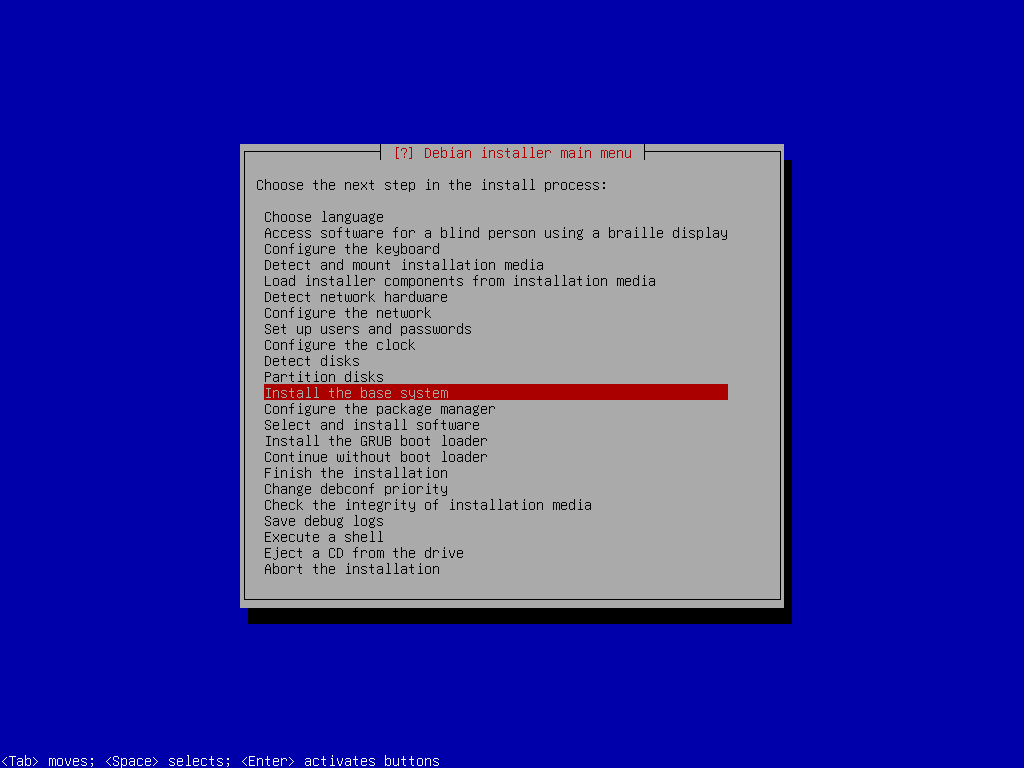
Base System Install
During the installation, you will be asked which kernel to install. When asked, select linux-image-amd64. You will also be asked which drivers to include, and you can choose generic ones. Once the installation is done, you can skip Configure the package manager and Select and install software packages.
The next step is Install the GRUB boot loader, but before we can install it, we need to instruct the GRUB we are using the encrypted disk. To do so, you will once again select Execute the shell from the main menu (press Enter to continue once you do):

Execute Shell
mkdir /target/etc/default/grub.decho "GRUB_ENABLE_CRYPTODISK=y" > /target/etc/default/grub.d/local.cfg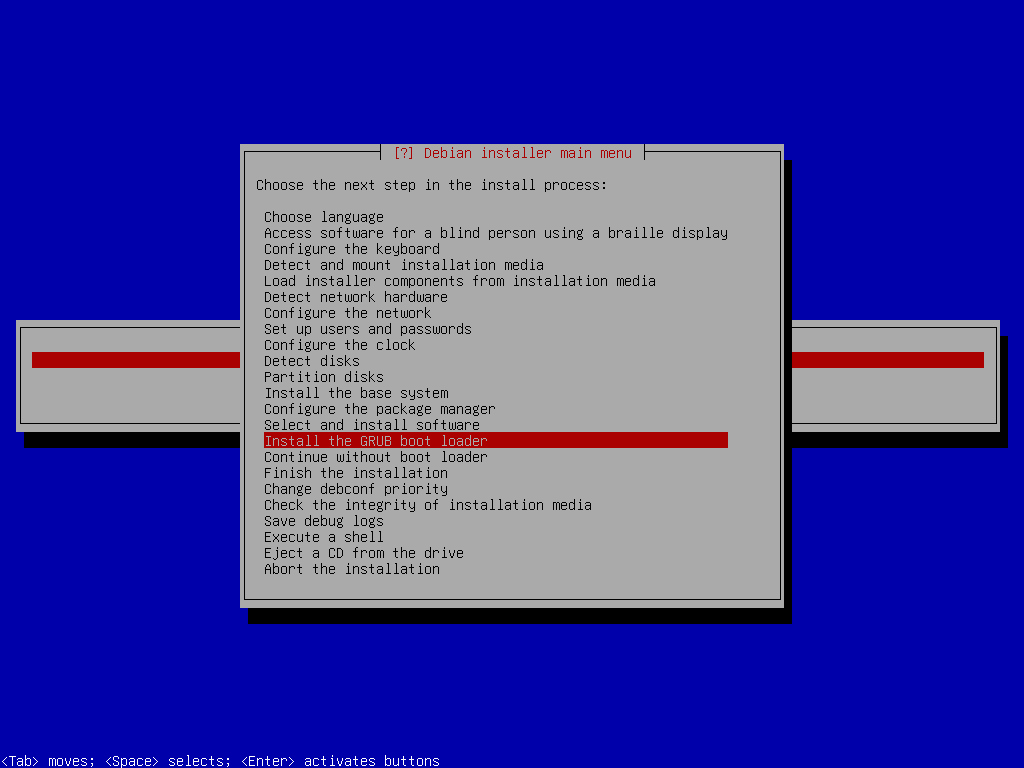
Install GRUB
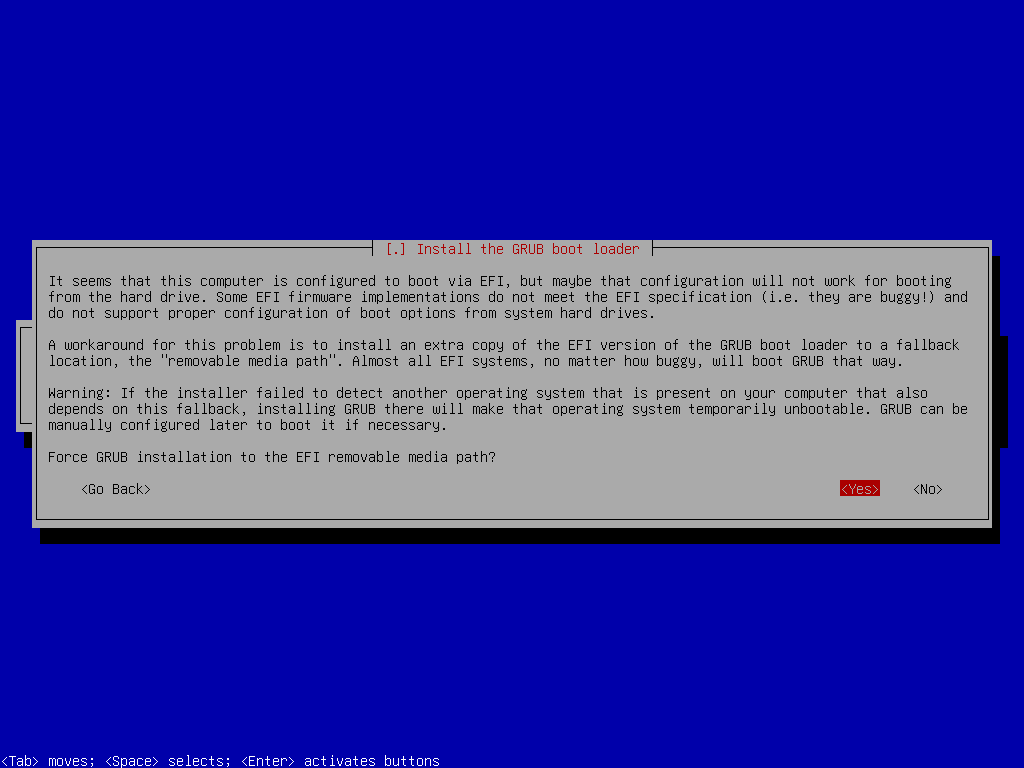
Install GRUB
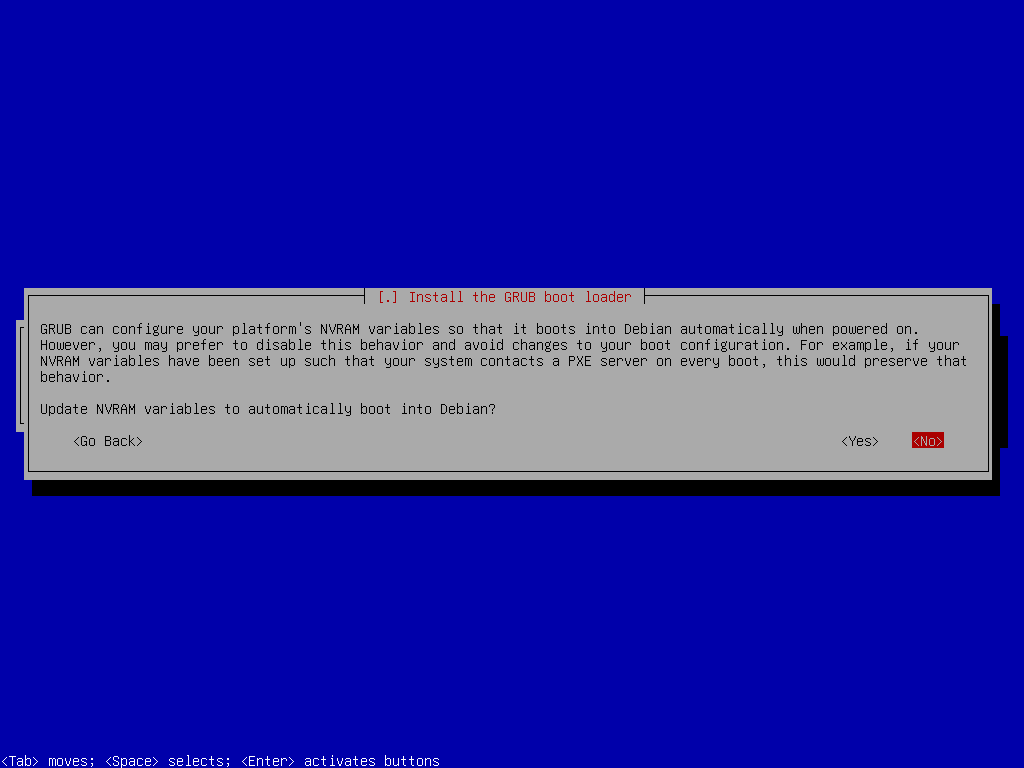
Install GRUB
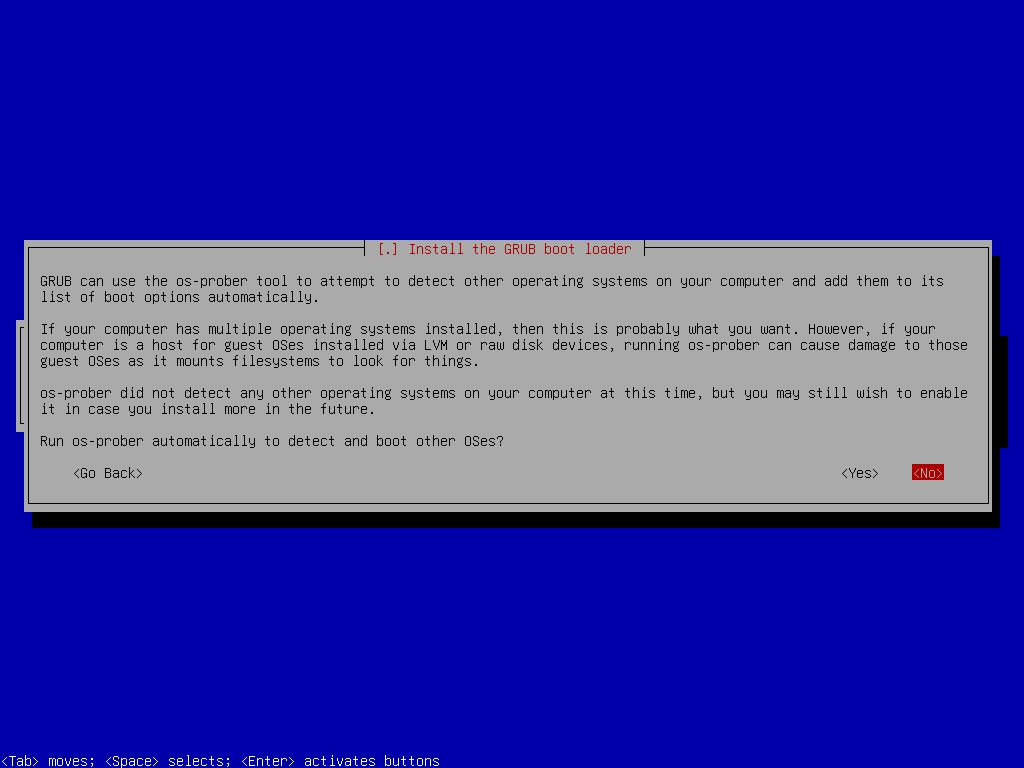
Install GRUB
Post Install Steps
One might say once GRUB is installed, we are done with the setup, but we're not quite yet. As a final step, you must add key files, which will automatically unlock the encrypted drive (after the passphrase input) to initramfs. The key files and supporting scripts are added to the/boot/initrd.img-$VERSION files. This is absolutely safe since these files are themselves stored in the encrypted /boot/, which is unlocked by the GRUB boot-loader (which asks you to type the passphrase), which then loads the kernel and initrd.img into RAM before handing execution over to the kernel.
To do so, first once again drop down to shell:

Install GRUB
mount /dev/mapper/vgdebian-root /target/root
for n in proc sys dev etc/resolv.conf; do mount --rbind /$n /target/root/$n; done
chroot /target/root
mount -aecho "KEYFILE_PATTERN=/etc/luks/*.keyfile" >> /etc/cryptsetup-initramfs/conf-hook
echo "UMASK=0077" >> /etc/initramfs-tools/initramfs.conf mkdir /etc/luks
dd if=/dev/urandom of=/etc/luks/boot_os.keyfile bs=512 count=1
chmod u=rx,go-rwx /etc/luks
chmod u=r,go-rwx /etc/luks/boot_os.keyfile
cryptsetup luksAddKey /dev/sda1 /etc/luks/boot_os.keyfile
cryptsetup luksAddKey /dev/sda4 /etc/luks/boot_os.keyfile echo "LUKS_BOOT UUID=$(blkid -s UUID -o value /dev/sda1) /etc/luks/boot_os.keyfile luks,discard" >> /etc/crypttab
echo "sda4_crypt UUID=$(blkid -s UUID -o value /dev/sda4) /etc/luks/boot_os.keyfile luks,discard" >> /etc/crypttabupdate-initramfs -u -k all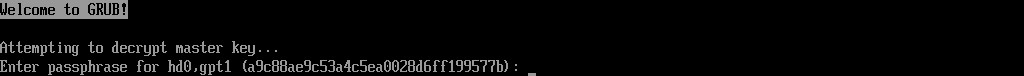
Enter Passphrase
You may also like
GNOME Customization on Debian: Complete Guide
Željko Jagušt